
Mobile endpoints are a significant risk vector for cyber attacks. More sophisticated cyber attacks by criminals, cyber vandals, state actors, extortionists, disgruntled employees and even corporate enemies require organisations to take mobile security seriously.
There are a variety of standards, certifications and recommendations in the cyber security field, so it is often difficult for organisations to know which ones to take notice of.
This article provides a short tour of some of the options, and translates an ACSC checklist into actionable objectives for any organisation wanting to fix cyber-security gaps in its mobile ICT.
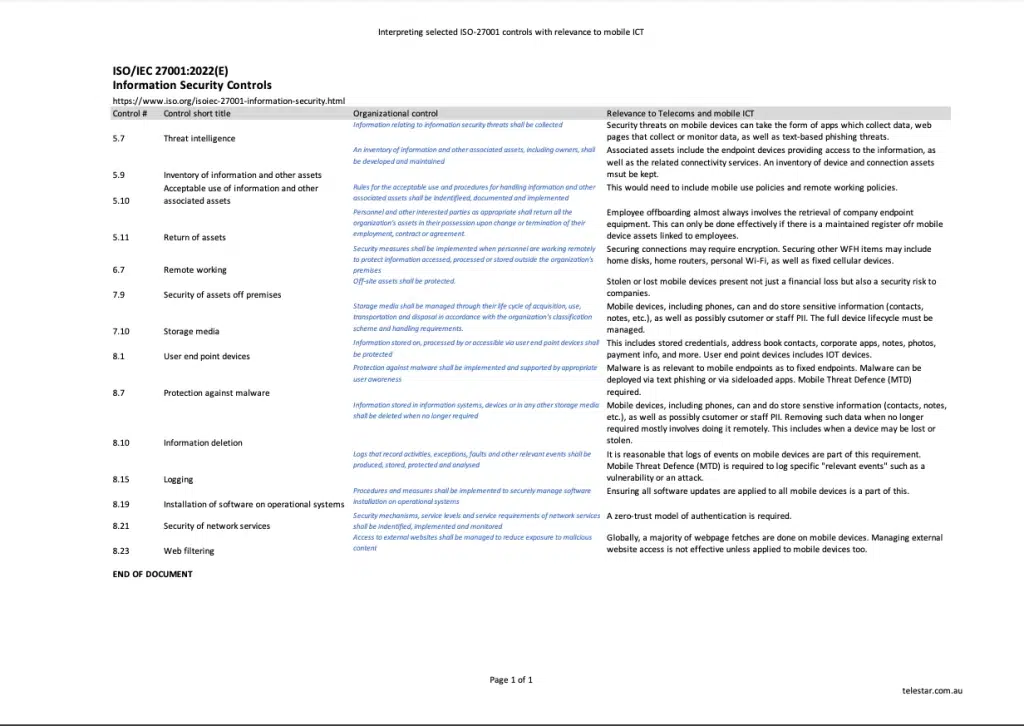
The best-known standard for Information Security is ISO/IEC 27001. 27001 certification requires a company to comply, and be audited against, a list of specific controls focused on information security process, policy and procedure.
However, 27001 does not generally differentiate between fixed (server-centric or data-room-centric or office-centric) information operations and those using remote access and equipment from mobile devices, either on the road or in a Work-From-Anywhere setting. This means that many of the requirements of 27001 may seem vague in a mobile context. Organisations often don’t think about the mobility aspect, or simply ignore it.
This handy table lists some of the 27001 controls which have direct relevance to mobility, and provides suggestions on how they could be implemented in mobility.
The “Essential Eight” maturity model is a security regime proposed by the Australian government’s Australian Cyber Security Centre which aims to provide a model around which organisations can build their cyber-security defences. It is a comprehensive approach, and is rightly well used in industry and government. It focuses on eight essential areas of protection:
| Application control |
| Patch applications |
| Configure Microsoft Office macro settings |
| User application hardening |
| Restrict administrative privileges |
| Patch operating systems |
| Multi-factor authentication |
| Regular backups |
Many organisations, however, miss the important context of the Essential Eight: that it is aimed at Windows-based (and primarily server-centric) networks, not mobility environments.
As the ACSC states:
“The Essential Eight has been designed to protect Microsoft Windows-based internet-connected networks. While the principles behind the Essential Eight may be applied to cloud services and enterprise mobility, or other operating systems, it was not primarily designed for such purposes and alternative mitigation strategies may be more appropriate to mitigate unique cyber threats to these environments. In such cases, organisations should consider alternative guidance provided by the ACSC.”
Attempting to apply the Essential Eight to mobile ICT operations is not without some merit, but it is not the best tool for the job.
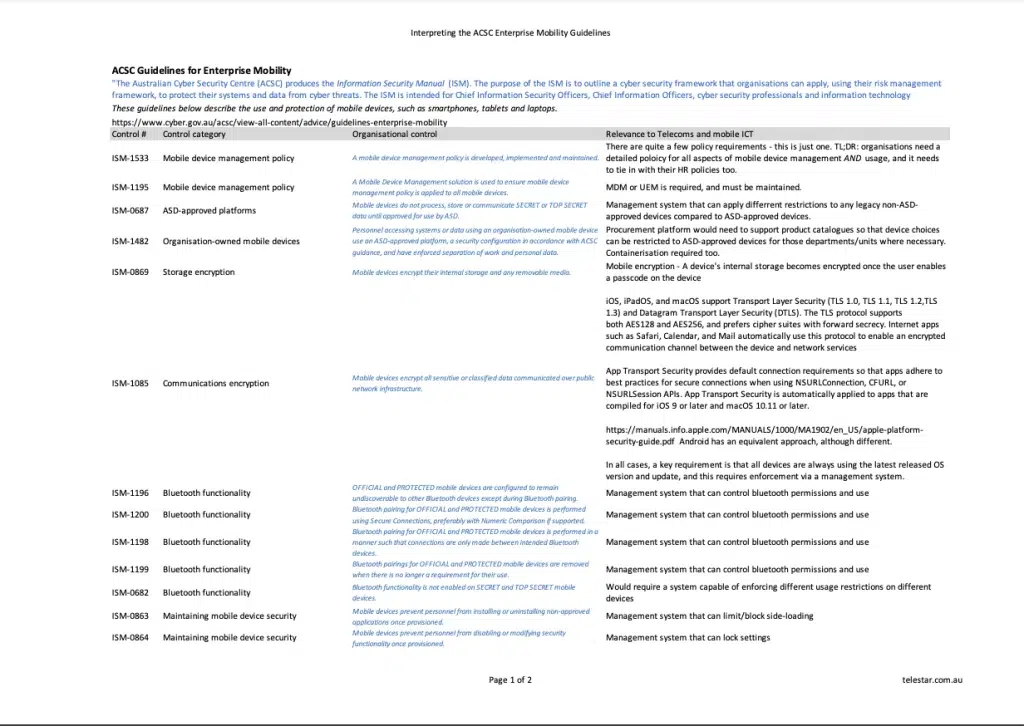
In response to the specific characteristics of mobile ICT, the ACSC provides a different tool: the ACSC Guidelines for Enterprise Mobility.
These guidelines use various controls from the ACSC’s Information Security Manual (ISM), the Australian government’s central cyber security checklist to help organisations protect themselves from cyber threats.
This checklist lists 19 key requirements (ISM controls) from the ACSC Guidelines for Enterprise Mobility. For each one, a brief explanation is offered on how this can be implemented in a corporate mobility environment, and what is required.
Telestar provides a comprehensive security service which implements and manages all the items in the guidelines. Our service can efficiently ensure your mobile ICT operations meet the ACSC guidelines, protecting your business continuity and the information of your organisation, clients and staff.
Telestar manages the telecoms and mobile ICT of enterprise and governments across Australia and New Zealand. With over half a million connections and devices under management, we understand the importance of mobile security.
Visit telestar.com.au or call us on +61 1300 658 687.