Mobile Device Management is riding a wave. Popularity amongst businesses for the software to control their smartphone fleets is higher than ever.
Recently, MDM providers have been given the type of PR opportunity they could only wish for, thanks to a very unlikely source.
The recent terrorist attack in San Bernardino, CA, left 16 people dead, including the two perpetrators. One of the perpetrators was a county employee who had been issued with a phone owned by the county. The FBI wants to search the phone for clues about other terrorists and future attacks, but it needs the phone’s manufacturer, Apple, to unlock the phone. The FBI has no warrant, and Apple has declined to help crack the phone, claiming that to do so would give the government tools capable of unlocking the private information of other phone users.
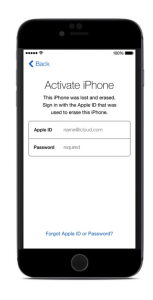
The FBI has argued that the phone is owned by the county rather than the employee, and that the county has consented, removing the need for a warrant. They want to do a brute-force attack on the phone’s password lock, but Apple’s operating system prevents this by limiting to ten wrong passwords before wiping the data. To decrypt this security would allow governments to spy on people’s data everywhere, says Apple.
The argument is becoming heated. Apple claims that to help the government would be a complete surrender of all their customers’ privacy everywhere. The FBI claims that Apple’s refusal is hindering the fight against terrorism and may cost lives in the future. They are probably both right, so the scene is set for an important test case.
However, overlooked in all this FBI-versus-Apple noise is the impact of MDM.
San Bernardino County does not use MDM on their mobile fleet – they bought one but have never used it. Many commentators have speculated on how things may have been different if they had. (You can read more about this here: Common software would have unlocked San Bernadino shooter’s iPhone.)
MDM could certainly have unlocked the county-owned smartphone. It could also have disabled it if and when desired. MDM could have controlled the apps on the phone, limited browsing options, and restricted usage. All of this may have been helpful at different moments in the San Bernardino case.
MDM can also do the opposite kinds of things too, like remotely wiping all the data from the phone. That’s not helpful in cases like San Bernardino, but is extremely helpful when an employee has a phone stolen (a much more common event than terrorism for most companies).
So that’s it then? Install MDM and everything is covered, right?
Not so much.
MDM, like any other management system, operates on rules. The quality of those rules is a bigger determiner of value than the system itself. With bad rules, even the best MDM can be of limited (or even negative) benefit.
Important rules to get right include which apps to permit for which employees, which activities to block for which employees, when to change permitted apps and activities, how to manage a device in a manner compatible with the carrier plan associated with it, when to lock a device versus when to wipe a device, and how best to control a surrendered device.
Think about that list for a few minutes, and it becomes obvious that a lot of business intelligence is required before a company can really make use of an MDM system.
For a start, most companies will have a variety of job categories with different mobility needs. Blocking a C-level exec from accessing certain functions can be as destructive as not blocking a lower level employee from certain apps. (For a recent high-profile example, read Self-inflicted security breaches.) But who decides? Where are these policies? And how do you handle change?
Unless you’re planning on hiring a small department of people just to manage your MDM, these aspects need to be automated within your organization, and linked. To not do so can be inefficient and expensive. (You can read more about this here: The true cost of managing mobility.)
The best MDM in the world won’t stop the waste of inadvertently allowing a junior employee to be set up with a high-end smartphone rather than a simpler device. Nor will it figure out by itself to re-configure the permissions on a device that has been re-assigned to a different level employee. Unless you want your star sales lead to be blocked from a critical app in the middle of her next on-site client demonstration, you better get these rules right, and then keep them right in a changing environment.
How many companies purchase an MDM system, but then months later are still not using it fully?
That’s because this stuff is hard. Working out your mobile policy, integrating the full mobile life-cycle, figuring out what person (or system) will co-ordinate all this on an ongoing basis – it’s all difficult and boring stuff. Buying an MDM is the easy part – about 20% of the problem – but then what?
The inflection point here is Managed Mobility Services. A Managed Mobility system integrates all aspects of mobility within an organization, and typically includes:
- Configuring of your mobility policy within a centralised system
- A cloud-based procurement portal and services catalogue, so that only role-appropriate device types and service types can be procured for each employee.
- A security console, giving instructions to your MDM system (or systems) and other security systems, and collating alerts from them
- Integrated feeds from your HR system (to capture employee adds, deletes, moves and changes in near real-time); your Asset system (to maintain a common view of all mobile devices available), your inventory system (to track all carrier services in operation), and your general ledger (for expense allocation).
- Expense analytics module, for verifying and analysing your communications expenses to identify areas for cost improvement dynamically
- A governance capability, to provide clear management views of all aspects of the mobility operation, across profiles, security and expenditure.
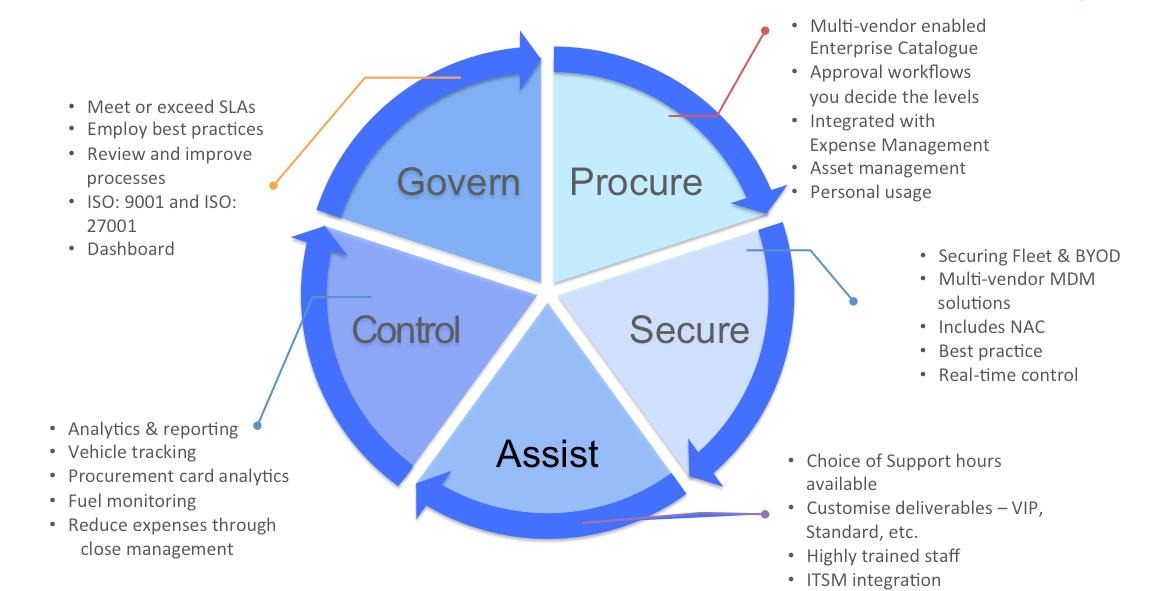
MDM is an important part of this picture, but only a part. Terrorist attack doesn’t happen to your business every day, but the need to manage security and efficiency does. To unleash the real benefits of MDM, it’s important to address the full picture of managing mobility.
Otherwise, like for San Bernardino County, your expensive MDM might end up being a nice shiny toy for your IT department, but delivering little business benefit.

